Cybersecurity threats often hide in plain sight, especially in email headers. A common tactic used by spammers, phishers, and attackers is masking their IP address to conceal their true origin.
If you’re an IT professional, sysadmin, or just someone tracing suspicious emails, learning how to detect masked IP address in email headers is essential.
1. What Is IP Masking and Why It Matters
Imagine someone calling your house using your friend’s phone so it looks like they’re your friend, but it’s really a stranger. That’s what happens when attackers mask their IP address in emails.
IP masking occurs when a user intentionally or automatically hides their actual IP address, often using tools like VPNs, proxies, TOR, or services like Gmail. This prevents traceability and is used for both privacy and malicious intent.
If you’re trying to detect masked IP address in email headers, you need to look beyond what’s visible at first glance, just like realizing the call didn’t actually come from your friend.
Example:
You receive an email from a “marketing consultant.” The header shows:
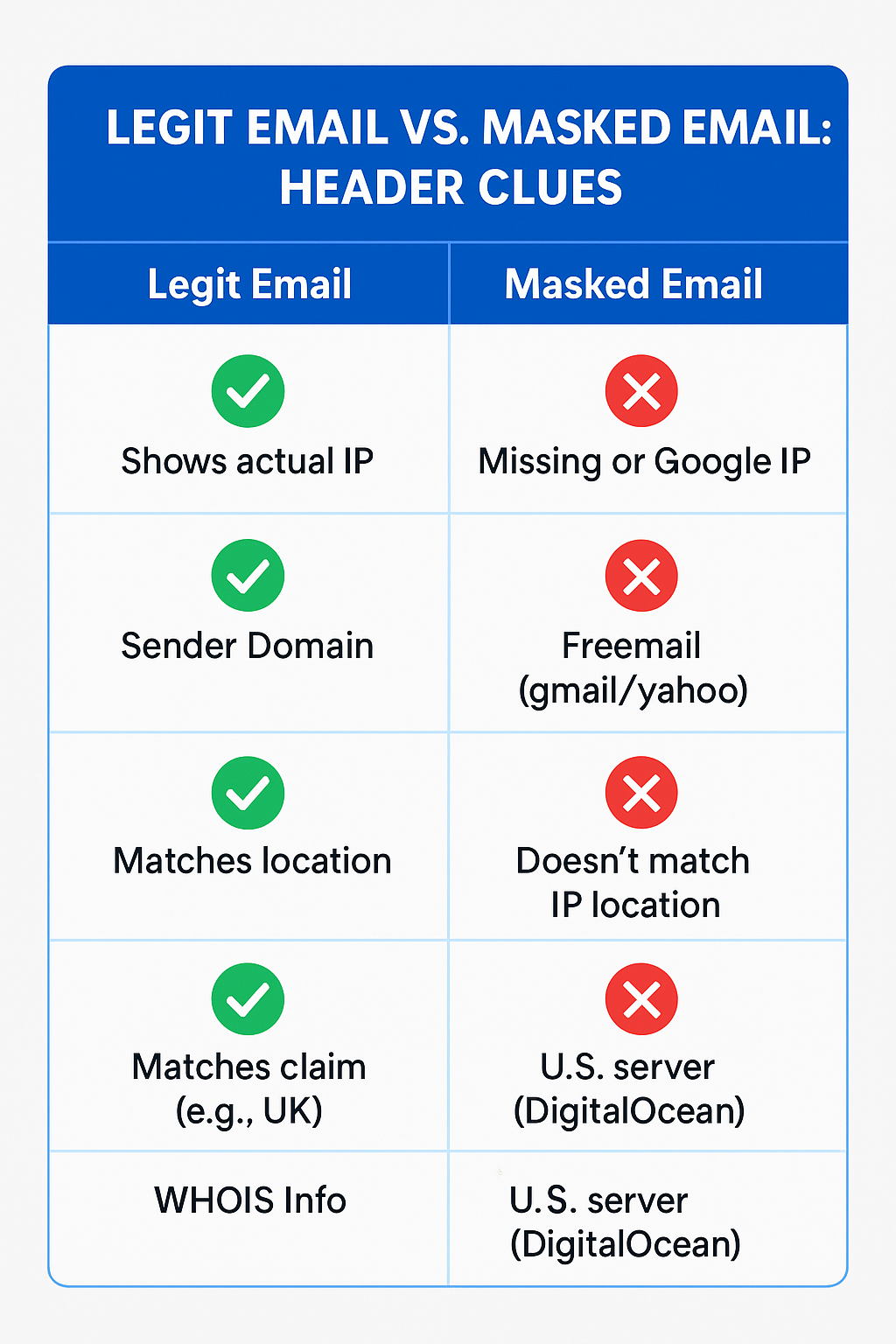
Received: from mail-yw1-f181.google.com ([209.85.128.181])
This IP belongs to Google, not the sender. They could be anywhere.
Solution: Understand that IP addresses from hosting giants or email providers often don’t reflect sender identity.
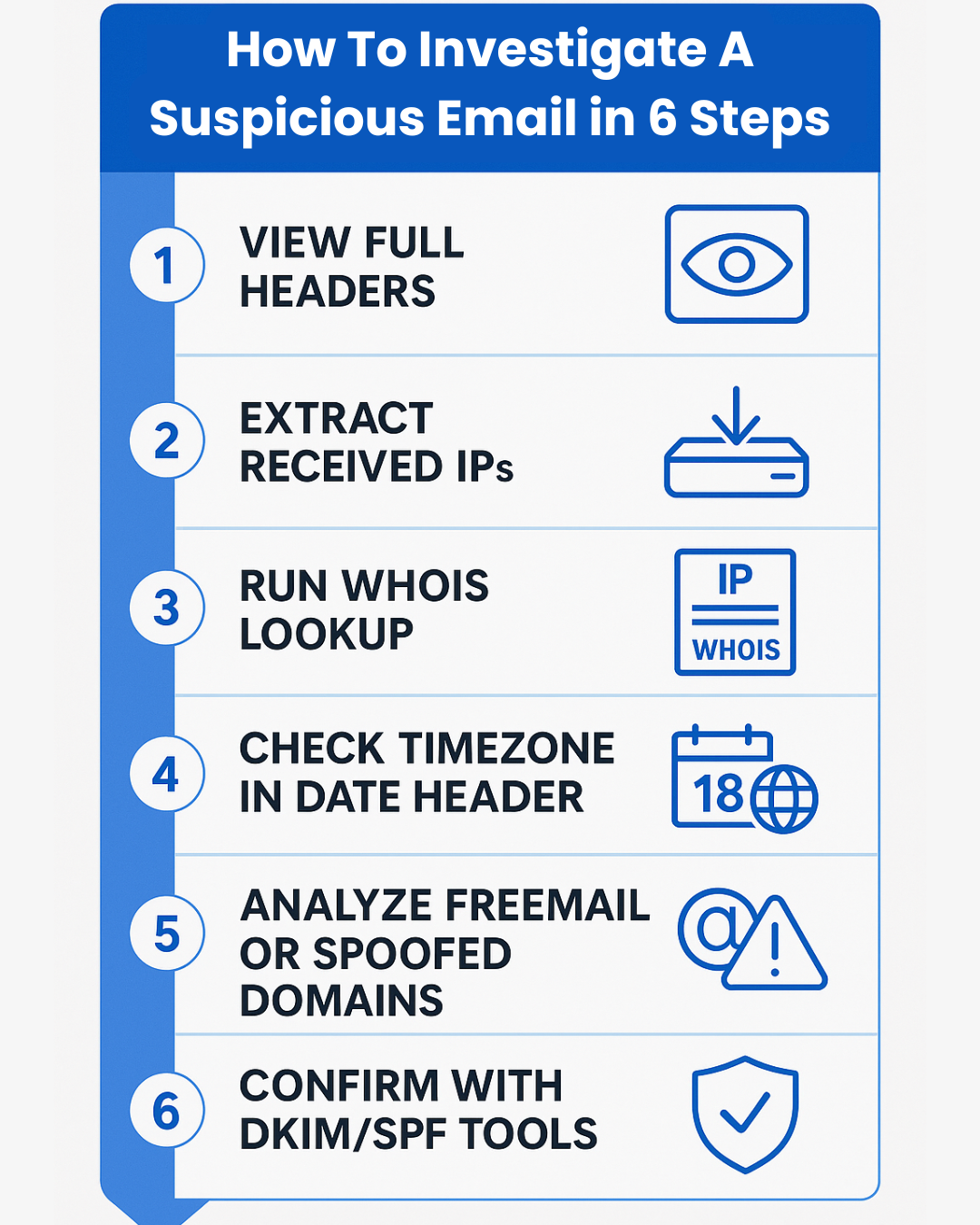
2. How to Reveal Full Headers in Gmail and Outlook
Full Headers in Gmail and Outlook: It’s like looking at a letter’s envelope and seeing where it came from, but if someone used a company mailbox, you can’t tell which person sent it.
To analyze the IP path, you need the full email headers.
Gmail:
- Open email → Click ⋮ (three dots) → “Show Original”
Outlook Web:
- Open email → Click ⋮ → “View message source”
Outlook Desktop:
- Open message → File → Properties → Internet headers
Look for:
Received: from ...
X-Originating-IP:
Problem: If only Google/Microsoft server IPs appear, the user IP is masked.
3. Use WHOIS/IP Lookup to Identify Ownership
You check a return address on a letter, and it says “Headquarters of Big Company,” not a person’s house. That means someone used a big building to mail it, but who was inside who sent it?
After finding the sending IP, look up its owner.
Example:
IP: 209.85.128.181
Use:
whois 209.85.128.181
Or:
Result:
{
"org": "Google LLC",
"city": "Mountain View",
"country": "US"
}
Clue: If the user says they’re from Germany, but the IP is Google-US, it’s masked.
4. Detect VPN/Proxy Providers in Headers
Imagine someone hides inside a delivery truck so you can’t see who’s really knocking on your door.
If the IP resolves to a hosting provider or VPN, it’s likely masked.
Example:
whois 45.32.123.4 | grep OrgName
Output:
OrgName: DigitalOcean, LLC
Or check domains like:
ec2-44-232-0-1.compute-1.amazonaws.com
Solution: Add known VPN providers to your firewall or email filter rules.
5. Use Timezone Mismatches to Spot Fakes
A kid says, “I’m in London,” but they send you a photo with the sun rising, and it’s midnight in London. Something’s off.
Check if the email’s Date: header timezone aligns with IP location.
Example:
Date: Tue, 1 Jul 2025 21:15:39 +0100
But IP: AWS server in US
Conclusion: +0100 = West Africa/UK timezone → mismatch → red flag.
6. Watch for Stripped or Missing Headers
It’s like someone tears off the return address from a letter; they clearly don’t want to be tracked.
Webmail like Gmail/Yahoo often hides sender IPs.
Example suspicious headers:
X-Originating-IP: [missing]
X-Google-Smtp-Source: AGHT+...
Legit desktop SMTP clients (e.g. Thunderbird) include:
X-Originating-IP: [105.112.23.90]
Tip: If headers look sanitized, assume webmail + masking.
7. Flag Freemail Use in Business Contexts
Business offers via free emails are a common scam pattern. You get a letter saying “I’m from a big toy company,” but it’s written on notebook paper, not company stationery. Seems sketchy.
Suspicious:
From: "Daniel" <toprankresults@gmail.com>
Professional:
From: Daniel <daniel@growthinsight.io>
Use command-line or regex to search headers:
grep -Ei "freemail|gmail|yahoo|hotmail" headers.txt
Add freemail domains to email filters for sensitive departments.
8. Validate SPF, DKIM, and DMARC Alignments
Use header validators to ensure sender authenticity. Imagine your teacher says a note is from your parents, but there’s no signature. Should you trust it? Probably not.
In email terms, tools like SPF, DKIM, and DMARC are the “signatures” that prove the message is really from who it claims. If one of them is missing or fails, it could mean the sender is spoofed, or trying to detect masked IP address in email headers becomes even more critical.
Example:
SPF: PASS
DKIM: PASS
DMARC: PASS
But:
DKIM: FAIL (no signature)
SPF: softfail
Use Tools:
Mismatch = likely spoofing or masking.
9. Ask for Alternative Verifications
When a sender seems shady, request non-IP-based proof. Even if someone says they’re in your town, they always show up late at night and say strange things. Doesn’t sound like someone local.
Ask for:
- LinkedIn profile with verified company
- Video Zoom call
- Email from a company domain (not freemail)
- Live dashboard/screenshare or document
Example:
If someone claiming to be a “HubSpot Partner” can’t show their portal or agency listing, walk away.
10. Analyze Behavior, Not Just Location
Even with IP masking, behavior reveals identity.
Watch for:
- Time of email replies (e.g. 3 AM in US but always daytime in Nigeria)
- Grammar/typo patterns
- Copy-paste signatures
- Reuse of proposals or scam templates
Tools:
- JStylo (https://psal.cs.drexel.edu/)
- Custom scripts for stylometry/writing fingerprinting
Result: Writing can unmask anonymous senders over time.
After learning header analysis techniques, why not reinforce your expertise with a professional certification?
Check out MockCertified’s IT security mock tests to boost your skills in digital forensics, network security, and threat analysis.
10 Lesser-Known Tricks to Detect or Counter IP Masking
While most people know the basics of spotting suspicious emails, attackers often go further by hiding their tracks through advanced IP masking techniques.
If you’re trying to detect masked IP address in email headers, these lesser-known tricks can give you an edge in uncovering the real source of an email, even when it seems untraceable.
- Use EmailRep.io to check sender trustworthiness
curl https://emailrep.io/fakepitch23@gmail.com - Check for tracking pixels using sandboxed email viewers
→ Use services like Mailtrap or Gmail’s download-as-EML option - Use Blacklist tools like Spamhaus, SORBS, or MXToolbox RBL
→ Input sender IP and check if it’s been flagged - Compare Received headers’ time drift
→ Sudden timestamp jumps may indicate relays across continents - Look for language inconsistency (e.g. UK spellings from a supposed US sender)
- Use stylometry on multiple messages to catch aliases
→ Compare writing from different Gmail accounts - Enable geo-fencing in your firewall or web portal (e.g. Cloudflare rules)
- Detect scripting in emails (automated bots use templates)
→ Look for similar structure, timing, format in multiple emails - Check domain registration age and ownership
→ Usewhoison suspicious company domains - Compare SMTP Message-ID pattern
→ Gmail:...@mail.gmail.comvs Self-hosted:...@mailer.youragency.com
Final Thoughts
Masked IPs are not inherently malicious, but they should never be trusted blindly. To detect masked IP address in email headers, combine header inspection, WHOIS checks, freemail flags, behavior profiling, and domain validation. Whether you’re managing cybersecurity, recruiting online, or filtering potential scams, these tools and techniques provide a robust defense against digital deception.